Data Breach or Security Breach: We often hear news of Data Breaches, Data Leak, Data Theft, Cyber Breach or Security Breaches commonly in the current digital and connected world. Sensitive information, such as private details, financial details, transaction details, trade secrets, and confidential business data, often stays at risk due to increasing phishing activities and cyber attacks throughout the world.
These data breaches can happen because of weak passwords, absence of right security measures, phishing scams, malware, insider threats, and many other incomplete security reasons. These data breaches and security attacks can lead to devastating consequences for individuals and organizations.
In this article, we will first understand “Data Breach”, then we will explore “Data breach types”, “Why data breach happens” and “How you can prevent it.” Let’s dive in.
Table of Contents
What is a Data Breach?
A data breach is theft of your data by unknown, unreliable and unwanted users. It happens when private or sensitive information is accessed, stolen, or leaked without permission by hackers, spammers, malicious organizations, or even by internal employees (mistakenly or intentionally).
Data security breach or theft can happen in many ways, such as through hacking of your systems, after receiving and opening phishing emails, SMS, spam messages or by Trojans, viruses and malware attacks. Hackers often target weak system defenses or vulnerable systems, which are not correctly protected or secure enough.
Few examples of data breach (data theft) include, breach of personal data like your name, address, social security number, email address, phone number and login credentials (usernames and passwords). This also include theft of financial data like debit card or credit card numbers and bank account information.
The consequences of a data breach can be severe for both individuals and businesses. It may result in huge personal or financial losses. Your hard earned can be stolen by using your financial information. Your personal information can be used for identity theft, doing a fraud, or other illegal acts, which is highly scary.
Moreover, data breaches can harm an organization’s reputation and brand deeply. It creates distrust among their employees and customers. This eventually leads to financial losses, and may result in legal and regulatory repercussions.
In order to prevent data breaches and cyber attacks, it is crucial for an individual and a company to seriously adopt the required proactive measures like:
- Using strong and unique passwords, by mixing letters, numbers, special characters and should be greater than 8 characters,
- Regularly updation of personal or company’s software to fix vulnerabilities,
- Use of trustworthy and powerful anti-virus and anti-spammers,
- Training staff and employees on regular basis to recognize phishing attempts,
- Installing reliable security tools like firewalls and antivirus software.
- If anyhow data breach occurs, respond quickly – such as by alerting everyone especially IT and operations team, follow their instructions or company’s anti-phishing policies or procedures, running antivirus software promptly, securing systems, and investigate the root cause of data breach.
These steps can help an organization in minimizing the damage done by data security breach and helps in preventing any further unauthorized access, which reduces the chances of data theft.
Data Breach Types
Data breach types or data leak faced by organizations and individuals can happen from variety of methods and sources used by the cyber attackers. Some of the most common types of data breaches are:
1. Hacking Attacks
Hacking is a type of cyber attack used by the hackers, it involves breaking into a computer systems or networks to steal or access private and sensitive information. Hackers may use a variety of techniques, to break into less secure systems exposing software vulnerabilities to gain unauthorized access to a system and steal the data.
2. Malware and Ransomware
Malware is a type of software that is designed to damage, disrupt or infiltrate computer systems. Malware programs are injected into systems which enables hackers to steal sensitive data, monitor a user’s activity, or control a system remotely.
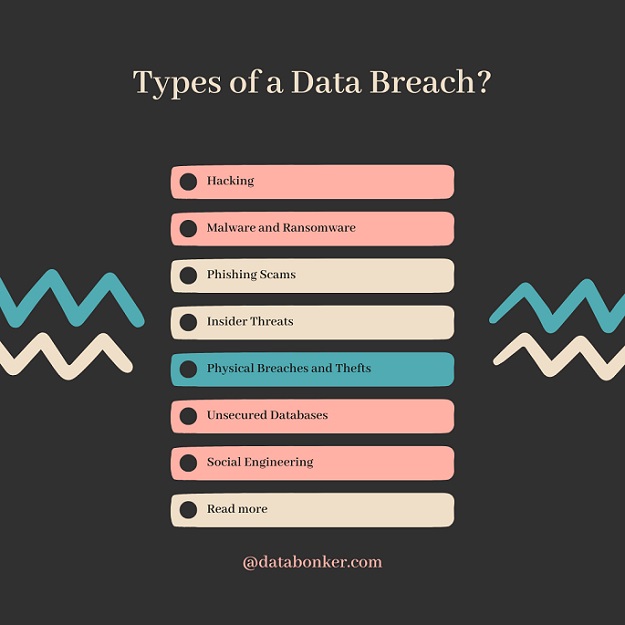
3. Phishing Scams
Phishing is a type of social engineering attack in which an attacker sends a fraudulent message or an email to trick the recipient into providing sensitive information.
Phishing emails and messages can be send to you through emails, social media platforms, or messaging apps. These emails reflect urgency and appear to be genuine. They prompt you to take a necessary action immediately, and then traps you by stealing your data or locking important files, until you fulfill their demands or pay a ransom. Be very careful, when you receive such kind of emails or messages.
4. Insider Threats
Insider threats are attacks that are carried out by authorized individuals or employees within an organization. These threats can be intentional or unintentional based on interests and can include stealing data, deleting data, or leaking sensitive information. Which can severely damage organization’s reputation and brand value.
5. Physical Breaches and Thefts
Physical thefts occur when physical devices such as smartphones, laptops, CDs, DVDs, SSDs or USB drives that contain sensitive information are lost or stolen. Which results in leak of valuable information.
6. Mis-Configuration and Unsecured Databases
When a system or application is not configured correctly, it may become vulnerable to get attacked by the hackers, spammers or dark web. Also, improperly secured databases can lead to unauthorized access by outsiders and may reveal sensitive information.
7. Social Engineering
Social engineering is also very common these days. It is a trick used by attackers to fool or deceive people into sharing sensitive information through spam messages, spam calls etc. These people act as trustworthy, but actually are deceivers who manipulates people and steal their private information.
These people generally involves in blackmailing, committing fraud and other malicious activities. Common social engineering fraud tactics include Pretexting, Baiting, and Quid Pro Quo.
8. Man-in-the-Middle (MITM) Attacks
MITM attacks generally happens over unsecured networks. In these attacks, hackers secretly intercept or hacks data being sent between two parties over an unsecured network, such as public Wi-Fi or insecure private WIFIs.
They can steal your login details, credit card information or other important details during an online transaction or when you connect your device to that network. To stay safe of these, always try to use secure websites (that starts with https:) and avoid using public networks (wifi).
9. Third-Party Breaches
A third-party breach occurs when a company’s vendor, supplier, partner or any other service provider has access to company’s sensitive information and gets hacked.
For example, if a payroll provider systems are hacked, company’s employees data might be stolen. Every business should ensure that their third-party partners follow strict security practices.
10. Cloud Storage Misconfiguration
This type of data breach happens when your cloud storage or your cloud service provider systems are improperly configured or are not enough robust to handle and stop spam activities.
By understanding the different types of data breaches and their root causes, organizations and individuals can implement appropriate security measures and build a secure ecosystem which allows data to flow freely among their users without any type of data breach.
Why Data Breach happens
In this section, we will try to understand the reasons, factors and root causes that lead to these data breaches and data leaks. Here are some of the common reasons:
- Cyber Attacks: Hackers and cyber criminals keep innovating and using different tactics to break into your systems. They use methods like hacking, phishing, malware, ransomware, baiting etc. The purpose is to gain unauthorized access to systems and steal sensitive data. These are one of the most common reason for data breaches around the world.
- Human Error: Simple human errors and mistakes, are the other common reason behind data breach such as sending data to the wrong person, incomplete security settings or setting up easy passwords etc.
- Insider Threats: Employees, staff or other insiders who have access to sensitive data can intentionally or unintentionally cause a data breach, may because of personal benefits or mistakes.
- Weak Passwords: Simple, weak or easy-to-guess passwords give hackers an easy way to access your accounts and systems.
- Outdated Software or Systems: Unpatched software and outdated systems are vulnerable by external or unwanted users. Outdated softwares and systems have outdated security files and thus can be easily broken by hackers.
- Risks Involved in Third-Party Services: Third-party vendors or partners who have access to an organization’s systems or data, but have insufficient security practices are another source for data breaches.
- Physical Theft or Loss: Physical theft or loss of devices such as laptops, USB drives and others can result in data breaches.
How to prevent a Data Breach
Preventing data breaches requires conscience and a multi-layered approach that involves understanding it’s reasons, ways and implementing various security measures. Here are some steps that you can take to prevent a data breach:
- Never open unidentified messages and emails: Be careful while opening messages unidentified and unrecognized messages or emails. Delete them, if you feel them as spam. Most importantly, don’t open any attachments attached with them.
- Avoid using public or insecure WiFi: We advice, that you shouldn’t use public or insecure WiFi’s otherwise utterly important. These are the common sources for data theft.
- Use strong passwords: Always use strong passwords that are difficult to guess. Keep updating your passwords regularly.
- Implement multi-factor authentication: Multi-factor authentication on your systems, accounts and emails adds an additional layer of security and makes it more difficult for hackers to gain unauthorized access.
- Encrypt sensitive data: Always keep your sensitive data as encrypted. Encryption makes your important data unreadable and unusable in the event of a data breach.
- Implement security software: Installing and regularly updating anti-virus software and firewalls can help protecting your systems from malware and hacking attacks.
- Educate or train your employees: Provide regular training sessions to employees and staff about these malpractices. Create a sense of awareness among them, as how to recognize phishing emails and other potential security threats. Educate them on how to deal with them efficiently.
- Limit access to sensitive data: Only provide sensitive information access to reliable and authorized individuals and keep updating credentials.
- Regularly update software and systems: Keep updating antivirus, firewall, spamming softwares and systems. So that, it can detect old as well as new viruses, malware’s and vulnerabilities that hackers can use to access your information.
- Conduct regular security audits: Regularly do security audits and take necessary actions. Regular security checks and audits can help identify potential vulnerabilities and help organizations to implement security measures for preventing data breaches.
- Implement a data breach response and action plan: There should be a data breach response plan placed in an organization ecosystem to respond, whenever such suspicious activity happens.
These steps can equip individuals and organizations to reduce the risk of data breaches and help in protecting sensitive information.
Impact of a Data Breach
Let’s examine the impact of a data breach on individuals and organizations data. Here are some of the potential impacts of a data breach:
- Financial losses: Data breaches can result in huge financial losses, which includes loss due to secret information, loss in tenders, loss of customers and clients and also the cost incurred to investigate the breach, time consumed, notifying affected individuals and customers, and implementing or updating security measures to prevent future breaches.
- Legal and regulatory penalties: Another crucial impact that organizations that experience have to face are legal and regulatory penalties for failing to protect sensitive data. Their are very strict government policies and heavy penalties on any such incident through-out the globe.
- Damage to brand reputation: Data breaches can damage an organization’s reputation severely, like loss of trust and confidence from customers, investors, and partners.
- Identity theft and fraud: Personal information that is exposed in a data breach can be used for identity theft and fraud. Which leads to personal and financial losses, damage to credit scores and you might come under radar of government investigation authorities.
- Disruption of business operations: Data breaches can disrupt or block business operations and flow, leading to less productivity and revenue.
- Loss of intellectual property: Data breaches can result in the loss of intellectual property, including trade secrets, patents, and proprietary information.
- Health and safety risks: If a data breach happens with drugs or patients data and cause leak of sensitive health and safety information. It can result in significant risks to individuals health and hampers their safety.
It is evident that the impact of a data breach can be far reaching, long lasting and more severe as it seems to be. It is important for individuals and organizations to stay careful and take proactive measures to prevent data breaches and cyber attacks. Your adequate preparation to respond quickly and take effective steps can help in making data and information, more safe and secure.
Examples of Data Breach
Let’s explore some important examples of data breach, that happened in the real world and created a stir with their subsequent effects:
1. Equifax Data Breach
In 2017, a big data breach happened at credit reporting firm Equifax. This resulted in data leakage of approximately 147 million people, including their names, Social Security numbers, birth dates, and addresses. This created a stir around the world, people started worrying about their data privacy and security.
This data breach was so big, that suffered Equifax huge losses. Later, the company reached a global settlement with the Consumer Financial Protection Bureau, the Federal Trade Commission and around 50 USA states and territories.
It’s settlement is still going on and recently in November, 2024, the settlement authority sent prepaid cards for payments settlements to the ones who earlier received it. You can see, how big it’s impact is.
You can read more about it on the official website of the US government, here : Equifax Data Breach update.
2. Retail Chain Target
In 2013, a big retail chain “Target” in United States had a massive data breach. This data breach had compromised 40 million credit and debit card numbers, along with the personal information of 70 million customers like their names, addresses, and phone numbers. All tis data became publicly available due to this data leak.
3. Yahoo
In another incident, big tech gaint “Yahoo” suffered two consecutive data breaches in 2013 and 2014. It affected data leakage of 3 billion user accounts personal information, including their names, email addresses, birth dates, and security questions.
4. Marriott International
In 2018, Marriott International reported a data breach that made publicly available names, addresses, phone numbers, passport numbers, and travel information of 500 million visitors.
5. Capital One
Financial services provider firm “Capital One” suffered a data breach in 2019. This data breach resulted in the leak of their 100 million clients and individuals data, including their names, addresses, credit ratings, and Social Security numbers.
6. Facebook
The social media tycoon “Facebook” also suffered a data breach in 2018, that resulted in the exposure of 87 million user’s names, birth dates, and email addresses.
These are just a few examples of data breaches, which occurred at very large scale. Many other organizations have also experienced similar incidents. Same is the case with many individuals, who suffered exposure of their personal data.
Data breaches are not a good thing, it can have severe impacts on individuals and organizations, financial and mental health. By taking precautions, swift and proactive measures combinedly by individuals, organisations and government authorities, we all can tackle it effectively.
Yojna Sharma works as an executive writer at DataBonker. She specializes in tracking latest & trending jobs, career events, and career opportunities. With extensive experience in tracking the latest industry trends, Yojna provides well-researched insights on job market updates, recruitment news, and professional growth opportunities, helping readers stay ahead in their careers.
📩 **Stay Ahead with DataBonker!**
Join our newsletter and get the latest insights on "Education, Admissions Guidance, Career Growth, Latest Job Trends, and Technology Updates** – straight to your inbox! 🚀

[…] important to keep your product key How to prevent Data Breach, as it serves as proof of ownership and is required if you ever need to reinstall the operating […]
[…] incidents of data breaches are happening now compared to earlier. This can harm businesses, governments, and individuals if […]
[…] The following are some common tasks involved in data wrangling: […]